MyInfo API (4.0.7)
Download OpenAPI specification:Download
MyInfo REST APIs for retrieving Person data.
Note - this specification is subject to changes based on evolution of the APIs.
4.0.7 (15 Apr 2025)
- Data Items
- New:
chas(Only on Singpass)
- Updated:
- vehicle enginecapacity field: Allow 0 for electric vehicle (EV)
- New:
- Data Items
4.0.6 (18 Mar 2025)
- Data Items
- Updated:
- drivinglicence pdl classes field: Updated max length to 3 characters
- drivinglicence qdl classes field: Updated max length to 3 characters
- Updated:
- Data Items
4.0.5 (17 Jan 2025)
- Data Items
- Updated:
- cpfcontributions employer name field: Updated max length to 100 characters
- cpfemployers employer name field: Updated max length to 100 characters
- Updated:
- Data Items
4.0.4 (29 Dec 2023)
- Data Items
- Updated:
- regadd building field: Updated max length to 65 characters
- Updated:
- Data Items
4.0.3 (02 Aug 2023)
- Updated URL for the RFC containing date information
- Updated overview and sequence diagrams
4.0.2 (31 Jul 2023)
- Operation
- Updated:
- Scheduled downtime
- Updated:
- Data Items
- New:
- ltavocationallicences.tdvl.licencename
- ltavocationallicences.tdvl.vocationallicencenumber
- ltavocationallicences.tdvl.expirydate
- ltavocationallicences.tdvl.status
- ltavocationallicences.pdvl.licencename
- ltavocationallicences.pdvl.vocationallicencenumber
- ltavocationallicences.pdvl.expirydate
- ltavocationallicences.pdvl.status
- ltavocationallicences.bdvl.licencename
- ltavocationallicences.bdvl.vocationallicencenumber
- ltavocationallicences.bdvl.expirydate
- ltavocationallicences.bdvl.status
- ltavocationallicences.bavl.licencename
- ltavocationallicences.bavl.vocationallicencenumber
- ltavocationallicences.bavl.expirydate
- ltavocationallicences.bavl.status
- ltavocationallicences.odvl.licencename
- ltavocationallicences.odvl.vocationallicencenumber
- ltavocationallicences.odvl.expirydate
- ltavocationallicences.odvl.status
- Updated:
- cpfinvestmentscheme scope updated to be retrieved by individual fields
- cpfinvestmentscheme.account
- cpfinvestmentscheme.saqparticipationstatus
- cpfinvestmentscheme.sdsnetshareholdingqty
- New:
- Operation
4.0.1 (31 Mar 2023)
- Data Items
- Updated:
- cpfcontributions.history employer field: Corrected max length to 30 characters
- cpfemployers.history employer field: Corrected max length to 30 characters
- Updated:
- Data Items
4.0.0 (3 Nov 2022)
- Security
- Introduced Proof Key for Code Exchange (PKCE) (RFC7636) to increase security posture between /authorize and /token call.
- Introduced JWKS endpoint to distribute Myinfo digital signing key(s).
- Test
- For token verification: https://test.authorise.singpass.gov.sg/.well-known/keys.json
- For data verification: https://test.myinfo.singpass.gov.sg/.well-known/keys.json
- Production
- For token verification: https://authorise.singpass.gov.sg/.well-known/keys.json
- For data verification: https://myinfo.singpass.gov.sg/.well-known/keys.json
- Test
- Replace Authorisation Security Header with Client Assertion for /token, and Demonstrating Proof-of-Possession (DPoP) token for /person API
- APIs
- Test:
- /com/v4/authorize
- /com/v4/token
- /com/v4/person/{sub}/
- /com/v4/person-sample/{uinfin}/
- Production:
- /com/v4/authorize
- /com/v4/token
- /com/v4/person/{sub}/
- Updated:
- /Authorize
- Updated /authorise to /authorize to conform to standards
- Updated 'purpose' to 'purpose_id'
- Renamed parameter 'attributes' to 'scope' to conform to standards
- Updated scope to be space(' ') separated to conform to standards
- Removed 'authmode' parameter
- Removed 'login_type' parameter
- Removed 'state' parameter
- Added mandatory field code_challenge
- Added mandatory field code_challenge_method (Only supports S256)
- /Token
- Removed Authorization field in HTTP header
- Added mandatory field DPoP in HTTP header
- Removed state field in body
- Added mandatory client_assertion field in body
- Added mandatory client_assertion_type in body
- Added mandatory code_verifier field in body
- /Person
- Removed 'txnNo' parameter
- Removed 'client_id' parameter
- Added 'iat' (issue at) and 'txnid' (transaction id) in JWS response from /person.
- Renamed parameter 'attributes' to 'scope' to conform to standards
- Scope is updated to be space(' ') separated to conform to standards
- Updated Authorization field prefix from bearer to DPoP in HTTP header
- Added mandatory field DPoP in HTTP header
- /Authorize
- Test:
- Data Items
- Updated:
- cpfbalances
- Updated data structure for each nested data item (i.e. cpfbalances.oa, cpfbalances.ma, cpfbalances.sa, cpfbalances.ra) to have its own set of 'classification', 'source' and 'lastupdated' fields
- cpfbalances.ra will appear with 'unavailable' flag set to 'true' if user does not have a Retirement Account
- cpfbalances
- New:
- childrenbirthrecords.sgcitizenatbirthind
- cpfmonthlypayouts
- cpfrstuselftopupamount
- cpfrstucurrentyeartaxrelief
- cpflife
- cpfmedishieldlife
- cpfbalances.oa
- cpfbalances.sa
- cpfbalances.ma
- cpfbalances.ra
- Removed:
- vehno
- workpassstatus
- workpassexpirydate
- mailadd
- billadd
- homeno
- edulevel
- gradyear
- schoolname
- householdincome
- Updated:
- Security
3.2.7 (26 Jan 2023)
- Data Items
- Updated:
- sponsoredchildrenrecords updated to include LTVP
- Updated:
- Data Items
3.2.6 (20 Dec 2022)
- Removed backchannel authentication.
3.2.5 (22 Nov 2022)
- Data Items
- Updated:
- Corrected attribute name from cpfdependentprotectionscheme to cpfdependantprotectionscheme
- Updated:
- Data Items
3.2.4 (3 Nov 2022)
- Data Items
- Updated:
- Description of 'Nationality' updated to 'Nationality/Citizenship'
- Description of Country updated to 'Country/Place'
- Updated:
- Operation
- Updated:
- Downtime
- Updated:
- Data Items
3.2.3 (22 July 2022)
- Data Items
- Updated:
- cpfhomeprotectionscheme: Corrected attribute response structure
- cpfdependentprotectionscheme: Corrected attribute response structure
- Updated:
- Data Items
3.2.2 (26 May 2022)
- Data Items
- New:
- cpfinvestmentscheme
- childrenbirthrecords.vaccinationrequirements
- sponsoredchildrenrecords.vaccinationrequirements
- hdbownership.purchaseprice
- hdbownership.outstandinginstalment
- Updated:
- Description of lastupdated to indicate that value may be blank if source agency does not have record for the user
- New:
- Data Items
3.2.1 (10 Feb 2022)
- Data Items
- New:
- merdekagen
- pioneergen
- cpfhomeprotectionscheme
- cpfdependentprotectionscheme
- Updated:
- regadd updated to include FIN registered address, which may also be unavailable.
- New:
- Data Items
3.2.0 (11 May 2021)
- Data Items
- New:
- partialuinfin
- academicqualifications
- cpfhousingwithdrawal
- Deprecated:
- mailadd
- billadd
- homeno
- edulevel
- gradyear
- schoolname
- householdincome
- Updated:
- Type enum for regadd (Unformatted to UNFORMATTED)
- Description of SG Address Block to 'Block/House of Address'
- Description for cpfcontributions to maximum of 15 months records
- marriagecertno to maximum 50 characters
- Local phone number default to '65'
- Employment Sectors of workpass to upper case, remove enumeration and provide examples of possible values
- Value of dob updated to include potential formats 'YYYY' and 'YYYY-MM'
- Removed code and desc fields from 'occupation' as these are SC/PR user provided fields. For FIN user's occupation, continue to use 'occupation.value'
- New:
- Security
- Certificate Authority list
- Comodo to Comodo/Sectigo
- New CA: Netrust
- Network
- Updated TLS version to only 1.2
- Updated recommended cipher suites
- Certificate Authority list
- Features
- Added 'appLaunchURL' request parameter in 'Authorise' API for launching mobile application after successful authentication using SingPass mobile
- Data Items
3.1.1 (4 December 2019)
- Updated path parameter 'uinfin' of person API to 'sub', indicating that the value of this parameter should come from the 'sub' attribute in access_token.
- Updated sample code 'createPersonRequest' function under person API to use 'sub' instead of 'uinfin'.
3.1.0 (16 September 2019)
- New data items available:
cpfemployerspartialuinfin
- New 'subentity' parameter in person API that allows traceability to platform's client who will be receiving the person data.
- Provide clarity on the handling of
housingtype&hdbtype
- New data items available:
3.0.2 (10 May 2019)
- Upper case all desc values for:
- Driving Licence : Comstatus, PDL and QDL Validity
- Children Birth Records: Sex
- Sponsored Children Records: Sex, Residential Status
- Person: Sex, Residential Status
- Upper case all desc values for:
- 3.0.1 (15 Apr 2019)
- Removed
serialnofrompdlandqdlunderdrivinglicenceas it is not in use. - Updated description for Understanding the Data Structure
- Removed
3.0.0 (31 Mar 2019)
IMPORTANT NOTE: response format for
personAPI has substantial changes from the previous version. Please refer to Understanding the Data Structure for details.- APIs updated to v3:
- Test:
- /com/v3/authorise
- /com/v3/token
- /com/v3/person/{uinfin}/
- /com/v3/person-sample/{uinfin}/
- Production:
- /com/v3/authorise
- /com/v3/token
- /com/v3/person/{uinfin}/
- Test:
- Response changes from JWE to JWE wrapping JWS
- Security header (changes in Authorization header parameters)
- Streamline header parameters to app_id, nonce, signature_method (RS256), signature, timestamp
- Standardisation of 'code', 'desc' and 'value' of all data items.
- New data items available:
- employmentsector
- passtype
- hdbownership
- sponsoredchildrenrecords
- vehicles
- drivinglicence
- Rename data items:
- workpassstatus -> passstatus
- workpassexpirydate -> passexpirydate
- Changes to the following data item to include "type" discriminator to discriminate local and foreign address. Format is significantly different between the two.
- regadd
- billadd
- mailadd
- Deprecated vehno attribute
- Updated scheduled downtimes: sandbox and test enviroments will no longer have any scheduled downtimes.
- APIs updated to v3:
The RESTful API adopts Semantic Versioning 2.0.0 for releases, and every new release of the API increments the version numbers in the following format:
{MAJOR}.{MINOR}.{PATCH}{MAJOR}number introduces incompatible API changes with previous{MAJOR}number also resets{MINOR}to0,{MINOR}number introduces new functionalities or information that are backward compatible also resets{PATCH}to0, and{PATCH}number introduces bug fixes and remains backward compatible.
Pre-release or draft versions, when provided, are denoted by appended hypen - with a series of separate identifiers {LABEL}-{VERSION} following the {PATCH} number. Such releases are unstable and may not provide the intended compatibility with the specification in draft status.
Serving as notice, the RESTful API in version 2.X.X are incompatible with version 1.X.X releases.
Despite backward compatibility in {MINOR} or {PATCH} releases, API consumers are best to evaluate and determine their implementation does not disrupt use-case requirements.
The following diagram illustrates how the integration with MyInfo APIs work:
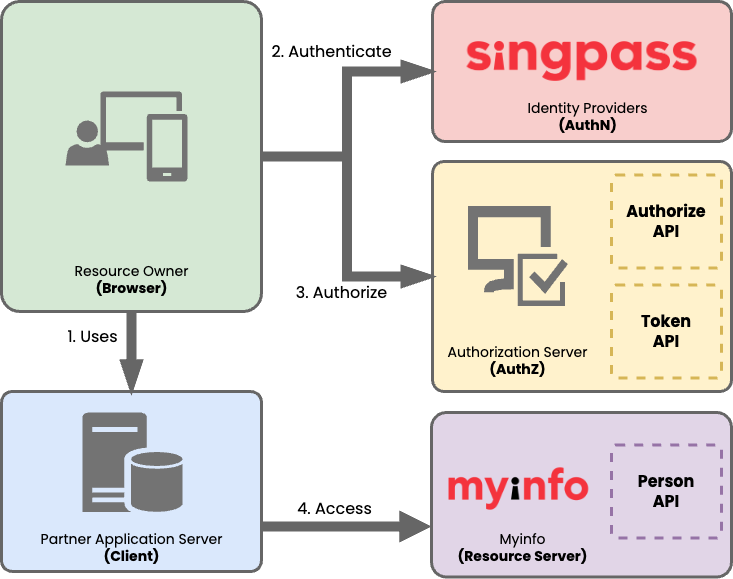
As shown above, partner's application will be interfacing with Myinfo's API Gateway to integrate successfully with MyInfo.
The RESTful APIs are provided in both testing and live environments, and are accessible over the Internet via HTTPS.
Consumers are to ensure firewall clearance on their edge network nodes for connecting to the APIs.
The convention used by API endpoints' URLs is in the following format:
https://{ENV_DOMAIN_NAME}/{CONTEXT}/{VERSION}/{RESOURCE}{ENV_DOMAIN_NAME}indicates MyInfo's API domain names - respectively:sandbox.api.myinfo.gov.sg, ortest.api.myinfo.gov.sg, orapi.myinfo.gov.sg, following
/{CONTEXT}, indicates the context of the API call =/com/{VERSION}indicates the endpoint's release{MAJOR}version number path - for this release =/v4/{RESOURCE}indicates the API resource path name. Any additional query string parameters are appended as needed.
1. Test Environment
The test enviroment is used for testing partner's application with the full security measures required in production. The Person API will return test data described in https://api.singpass.gov.sg/library/myinfo/developers/resources-personas.
Note:
- Domain Name:
test.api.myinfo.gov.sg - Client assertion, DPoP Proof JWT and PKCE are required in Token API.
- Authorization DPoP-bound access token and DPoP Proof JWT are required in Person API.
- Authorization DPoP-bound access token should be verified by partner's application.
2. Production Environment
The production enviroment is the actual live environment with full security measures and live data.
Note:
- Domain Name:
api.myinfo.gov.sg - Client assertion, DPoP Proof JWT and PKCE are required in Token API.
- Authorization DPoP-bound access token and DPoP Proof JWT are required in Person API.
- Authorization DPoP-bound access token should be verified by partner's application.
The following are the scheduled downtimes for the various environments:
Production Environment
CPFB data
- Every day 0500hrs to 0530hrs
- Every 1st Sun of the month from 0000hrs to 0800hrs
- Every 4th Sun of the month from 0000hrs to 0800hrs
IRAS data
- Every Wed, 0200hrs to 0600hrs
- Every Sun, 0200hrs to 0830hrs
MOM data
- Every 4th Sun of the month from 0000hrs to 0600hrs
Test Environment
- none
API Security
PKCE (V4)
PKCE is introduced to protect against authcode injection attacks by requiring partners to prove to the authorization server that the authcode belongs to them in order for the authorization server to issue access token. This is achieved by code challenges and code verifiers exchanged during the /authorize and /token call respectively.
PKCE replaces the use of 'state' parameter. Partners are required to manage a session to their frontend to link the code_verifier and code_challenge.
Client Verification
JWKS(V4) vs Certificate(V3)
Instead of relying on certificates uploaded during onboarding, partners will now need to specify their respective JWKS (JSON Web Key Set) URLs in order for /token call to retrieve the partner's public_signing_key used to verify client assertions signatures and for /person call to retrieve the partner's public encryption key used to encrypt the data.
Sample JWKS:
{
"keys": [
{
"use": "sig",
"alg": "ES256",
"kty": "EC",
"kid": "vPT7o62ke_t4dTUQQwDhcFw_hX_FbiwFS3eCvYC2yz8",
"crv": "P-256",
"x": "jbqsZUCAf_Sj1oq6jR0ErpzIGbiAJ_GgHkZ18YeOgGE",
"y": "xB2rsB3a8xug6eiacWrxoTNJi92hyO1eNccpKBGjqdo"
},
{
"use": "enc",
"alg": "ECDH-ES+A256KW",
"kty": "EC",
"kid": "iop1ls7rt-Y1jmFXTWsxxb3TKKgxwB566V2pUVJdjVY",
"crv": "P-256",
"x": "bqYdlztg_OhQt2a-ocr05Feu6nHXFVZ2oy7R750t3TA",
"y": "Suu4cYvK0rH6njN_1Q2utIYrEffDYCtzFyxdcI2nrfM"
}
]
}This approach allows partners to manage keys autonomously and enables minimal disruption during key rotation (JWKS holding multiple keys at the same time). Myinfo has similarly introduced JWKS endpoints to distribute our public signing keys for partners to perform signature verification. This will enable minimal disruption for partners during Myinfo's key rotation.
For performance reasons, NDI caches the keys found in the partners' JWKS endpoint for one hour. When partners' signing keys need to be rotated, new keypairs must use different key id (kid) values and maintain both old and new keys in the JWKS for at least an hour.
Client Assertion(V4) vs Base String Signing(V3)
Taking reference from RFC7251, Client Verification in v4 relies on Client Assertion as opposed to checking signature of a formulated Base String. Though the verification mechanism remains unchanged i.e. checking of digital signature, Client Assertion is more aligned to international standards.
Together with the Client Assertion, partners will need to provide a DPoP Proof JWT in the HTTP header with an ephemeral public signing key, which is used in the /person call for verification of access token possession.
DPoP(V4) vs Base String Signing(V3)
During /person call, partners will need to generate DPoP Proof JWT that correspond to the access tokens received to prove legitimacy of possession before data can be released. The DPoP token will be signed using the partner's ephemeral private signing key and Myinfo will check using the partner's ephemeral public signing key provided previously in the /Token call.
MyInfo's API gateway supports accessing of APIs via the following interfaces:
HTTP version 1.1 connection over TLS (Transport Layer Security) version 1.2 standards, and cipher suites:
- using AES (Advanced Encryption Standard) and SHA (Secure Hash Algorithm),
- on either GCM (Galois/Counter Mode) or CBC (Cipher Block Chaining) mode.
Below is the list of recommended cipher suites that partners may use:
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
IMPORTANT: ensure partner's server supports TLS 1.2 and supports a cipher suite in the list above.
Accessing the RESTful APIs using prior versions of TLS and/or unsupported ciphersuites will result in connectivity errors. MyInfo's API gateway does not support 2-way TLS client nor mutual authentication.
API HTTP interface features:
- JSON (JavaScript Object Notation) is the supported data media format and indicated in
Content-Typeheaderapplication/json, also Content-Lengthheader is omitted by havingTransfer-Encodingheaderchunkedemitted for streaming data, and- GZip (GNU Zip) response compression is supported by opt-in
Accept-Encoding: gzipand indicated inContent-Encodingheadergzip.
MyInfo APIs use OAuth2.1 authorisation code flow to perform authentication & authorisation.
The sequence diagram below illustrates the steps involved in integrating partner's application with Myinfo APIs:
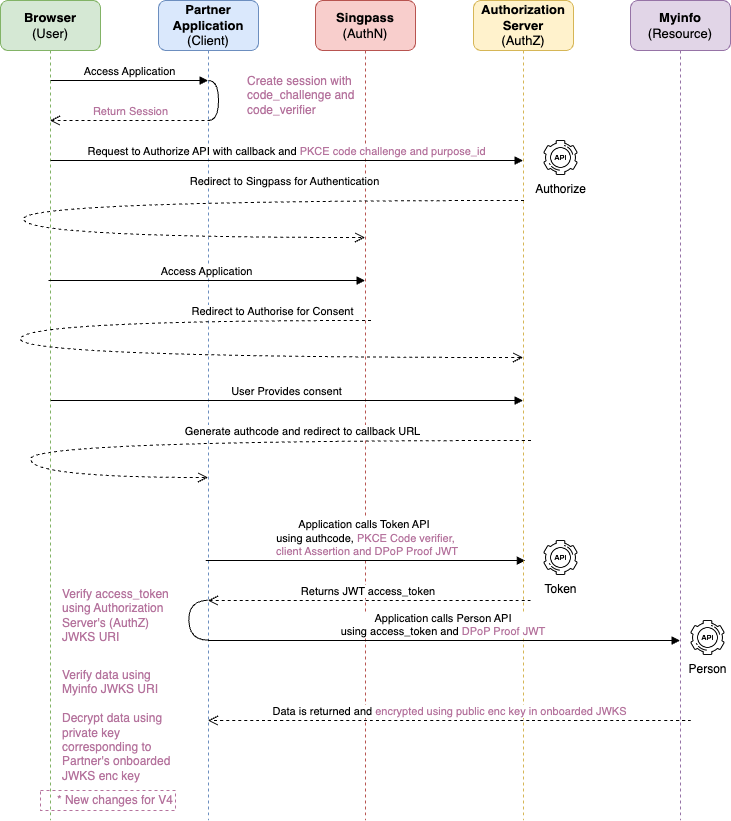
The flow consists of 3 APIs:
Authorise
- This will trigger the SingPass login and consent page. Once successful, partner's application will receive the authorisation code via partner's callback url.
Token
- Call this server-to-server API with a valid authorisation code to get the access token.
Protected Resource (Person)
- Call this server-to-server API with a valid access token to get the person data.
PKCE is an extension to the Authorization Code flow to prevent CSRF and authorization code injection attacks (Refer to https://datatracker.ietf.org/doc/html/rfc7636). The mechanism relies on 2 parameters namely code_challenge (base64(sha256(code_verifier))) and code_verifier (cryptograhic random string generated and kept secret on serverside) sent in the authorize and token call respectively to enable the Authorisation Server to perform correlation. Below is an example of how code_verifier and code_challenge are produced on server side. The code_challenge can then be attached to the authorize call.
Sample Code in NodeJS
function base64URLEncode(str) {
return str.toString('base64').replace(/\+/g, '-').replace(/\//g, '_').replace(/=/g, '');
}
function sha256(buffer) {
return crypto.createHash('sha256').update(buffer).digest();
}
function generateCodeChallenge(codeVerifier) {
try {
let codeChallenge = base64URLEncode(sha256(codeVerifier));
return codeChallenge;
} catch (error) {
// error handling
throw (error);
}
}
var codeVerifier = base64URLEncode(crypto.randomBytes(32)); var codeChallenge = generateCodeChallenge(codeVerifier);Authentication methods provided by Myinfo on internet:
- OAuth 2.1 using
Client Assertion(see "Client Assertion" section below) - Client Assertion should be signed using a key that is published on partner's JWKS endpoint, which is submitted during client onboarding.
The Partner's application is required to generate client assertions to be attached to server-to-server calls to prove authenticity (Refer to https://datatracker.ietf.org/doc/html/rfc7521). The partner's private key signs the assertion metadata, and Myinfo will use the partner's onboarded JWKS endpoint to obtain the public key for verification.
Below is a sample of the JWT header and payload of the client assertion:
{
"typ": "JWT",
"alg": "ES256",
"kid": "x0zDLIC9yNRIXu3gW8nTQDOMNe7sKMAjQnZj3AWTW2U",
} . {
"sub": "PROD2-MYINFO-SELF-TEST",
"jti": "jNDZuyLw66gkTjmCNMawzrTJNlhS8wdjpU0DHTzo",
"aud": "https://api.myinfo.gov.sg/com/v4/token",
"iss": "PROD2-MYINFO-SELF-TEST",
"iat": 1662365106,
"exp": 1662365406,
"cnf":{
"jkt": "G_q8Qv9-xv_9xJo-esolTnvxVSobMER7O0LKGPBlTqY"
}
}{sub}Subject - client_id issued by Myinfo upon onboarding{jti}JWT ID - random unique identifier{aud}Audience - URL that partner's application is calling{iss}Issuer - client_id issued by Myinfo upon onboarding{iat}Issued At - current timestamp{exp}Expiry - expiry timestamp, maximum 300 seconds (5 minutes){cnf.jkt}JWK Thumbprint - base64url encoding of the JWK SHA-256 Thumbprint of the partners's ephemeral public signing key used to sign the DPoP Proof JWT
Sample post body with DPoP Proof and client assertion
Below is an example of a post body of a token API call:
// Response body of token call in a transaction
POST /token HTTP/1.1
Host: api.myinfo.gov.sg
Content-Type: application/x-www-form-urlencoded
DPoP: eyJ0eXAiOiJkcG9wK2p3dCIsImp3ayI6eyJrdHkiOiJFQyIsImtpZCI6IkdfcThRdjkteHZfOXhKby1lc29sVG52eFZTb2JNRVI3TzBMS0dQQmxUcVkiLCJjcnYiOiJQLTI1NiIsIngiOiJPMTRHMXVlUjBTeHRSNGRsVW9rZ1FzMmM3NXFLV1VXSVRLWDYwaXYwTHkwIiwieSI6IlMzQjhSUC1OaGc2dTBMTE43Y0ZfX2lzUmctQVNHcFp3WTN4V2JrQVFRWXMiLCJ1c2UiOiJzaWciLCJhbGciOiJFUzI1NiJ9LCJhbGciOiJFUzI1NiJ9.eyJodHUiOiJodHRwczovL3NpdC5hcGkubXlpbmZvLmdvdi5zZy9jb20vdjQvdG9rZW4iLCJodG0iOiJQT1NUIiwianRpIjoib3MyWk14cEZVMnpISm9aTWhXbkFaeWRwcWYyM0JsZ3dDTkFFcmptRyIsImlhdCI6MTY2MjM2NTEwNiwiZXhwIjoxNjYyMzY1MjI2fQ.X69HdF8C_9IRAeDGG9kr7ViV4SGyH7G4ovm_pTlvHwQaLJvr4f4Lf445h-2aPt06kPagnfuO4-HgctRalxThqw
grant_type=authorization_code&
code=5uHGo2QpNAG99gO6rjqtzNuzrdnzJwatjpeuejvB&
redirect_uri=http%3A%2F%2Fmyapp.com%2Fcallback&
client_id=STG2-MYINFO-SELF-TEST&
code_verifier=ZK2mVhN9gBY9aGytuTIYmU7yHMueb7jZxMrE4WzjRRU&
client_assertion_type=urn%3Aietf%3Aparams%3Aoauth%3Aclient-assertion-type%3Ajwt-bearer&
client_assertion=eyJ0eXAiOiJKV1QiLCJhbGciOiJFUzI1NiIsImtpZCI6ImFRUHlaNzJOTTA0M0U0S0Vpb2FIV3ppeHQwb3dWOTlnQzlrUkszODhXb1EifQ.eyJzdWIiOiJTVEcyLU1ZSU5GTy1TRUxGLVRFU1QiLCJqdGkiOiJqTkRadXlMdzY2Z2tUam1DTk1hd3pyVEpObGhTOHdkanBVMERIVHpvIiwiYXVkIjoiaHR0cHM6Ly9zaXQuYXBpLm15aW5mby5nb3Yuc2cvY29tL3Y0L3Rva2VuIiwiaXNzIjoiU1RHMi1NWUlORk8tU0VMRi1URVNUIiwiaWF0IjoxNjYyMzY1MTA2LCJleHAiOjE2NjIzNjU0MDYsImNuZiI6eyJqa3QiOiJHX3E4UXY5LXh2Xzl4Sm8tZXNvbFRudnhWU29iTUVSN08wTEtHUEJsVHFZIn19.OuXR4qOmY8Lilqf6QcgC7PW1hRAgWoG41gHdSC4N-6UiipH1kgdXynazq0rF5JxqOi0Bxah4Jh41KbgEoJ3geQ
Sample Code in NodeJS that generates the DPoP Proof and client assertion
async function generateClientAssertion(url, clientId, privateSigningKey, jwkThumbprint){
try {
let now = Math.floor((Date.now() / 1000));
let payload = {
"sub": clientId,
"jti": generateRandomString(40),
"aud": url,
"iss": clientId,
"iat": now,
"exp": now + 300,
"cnf" : {
"jkt": jwkThumbprint
}
};
let jwsKey = await jose.JWK.asKey(privateSigningKey, "pem");
let jwtToken = await jose.JWS.createSign({ "format": 'compact', "fields": { "typ": 'JWT' } }, jwsKey).update(JSON.stringify(payload)).final();
logger.info("jwtToken", jwtToken);
return jwtToken;
} catch (error) {
logger.error("generateClientAssertion error", error);
throw constant.ERROR_GENERATE_CLIENT_ASSERTION;
}
};
async function generateJwkThumbprint(ephemeralPublicKey){
let jwkKey = await jose.JWK.asKey(ephemeralPublicKey, 'pem');
let jwkThumbprintBuffer = await jwkKey.thumbprint('SHA-256');
let jwkThumbprint = jose.util.base64url.encode(jwkThumbprintBuffer, 'utf8');
return jwkThumbprint;
}
async function generateEphemeralKey() {
let options = {
"namedCurve": "P-256",
"publicKeyEncoding": {
"type": "spki",
"format": "pem"
},
"privateKeyEncoding": {
"type": "sec1",
"format": "pem"
}
};
ephemeralKeyPair = crypto.generateKeyPairSync("ec", options);
let ephemeralPublicKey = (await jose.JWK.asKey(ephemeralKeyPair.publicKey, "pem")).toJSON();
ephemeralPublicKey.use = "sig";
ephemeralPublicKey.alg = "ES256";
return ephemeralPublicKey;
}Partner's application is required to generate DPoP Proof JWT to be attached to server-to-server resource calls to prove the legit possession of the access token. (Refer to https://datatracker.ietf.org/doc/html/draft-ietf-oauth-dpop). The token is signed by partner's ephemeral private signing key, which the partner's public signing key had been used in the token call and "embedded" into the access token provided.
Below is a sample of the JWT header and payload of a DPoP token:
{
"typ": "dpop+jwt",
"alg": "ES256",
"jwk": {
"kty": "EC",
"kid": "CRx5jixF8ZLRpxpqguxCwiq0g6b-ACHfQQJT7uiAkio",
"crv": "P-256",
"x": "mxVK8wvCaQ8iUJ4AyZr1oK1_ceL_27kgTPISNEcChm4",
"y": "0P-81zpWvcy6YAPSiV_K4h94wdEdk-RwrhbTL0fkeyc"
}
}
. {
"jti": "dfgsrtsDFBBgbsB230afktmdFGdgegemmet",
"htu": "https://api.myinfo.gov.sg/com/v4/person/08939d6c-11c0-4bc9-b2cd-f5fd14369521",
"htm": "GET",
"iat": 1645757787,
"exp": 1645757907,
"ath": "RyPeyISsEqdR1lsZBv80o0A8eF1Kvxdm_uf1hnLRf9M"
}
{typ}Type - Type (Header), value "dpop+jwt"{alg}Algorithm (Header) - digital signature algorithm identifier as per RFC7518 (Refer to https://datatracker.ietf.org/doc/html/rfc7518). MUST NOT be none or an identifier for a symmetric algorithm (MAC).{jwk}JSON Web Key (Header) - public key chosen by the client. MUST NOT contain the private key.{jti}JWT ID (Payload) - unique identifier{htu}HTTP URL (Payload) - HTTP URI used for the request, without query (?) and fragment parts (#){htm}HTTP Method (Payload) - HTTP method for the request to which the JWT is attached{iat}Issued At (Payload) - current timestamp{exp}Expiry (Payload) - expiry timestamp{ath}Access token hash (Payload) - The base64url encoded SHA-256 hash of the ASCII encoding of the associated access token's value (Required only for /Person call after DPoP-bound access token is issued)
Sample Code in NodeJS that generates the DPoP token
//function to generate the base64url encoded SHA-256 hash of the ASCII encoding of the accesstoken
function generateAth(accessToken){
let sha256AccessToken = crypto.createHash('sha256').update(accessToken).digest();
let base64URLEncodedHash = sha256AccessToken.toString('base64').replace(/\+/g, '-').replace(/\//g, '_').replace(/=/g, '');
return base64URLEncodedHash;
};
// generates DPoP Proof JWT headers for calling **Person** API
async function generateDpopProof (url, method, sessionPopKeyPair, ath) {
try {
let now = Math.floor((Date.now() / 1000));
let payload = {
"htu": url,
"htm": method,
"jti": generateRandomString(40),
"iat": now,
"exp": now + 120,
};
//required only for /Person resource call
if(ath)payload.ath = ath;
let privateKey = await jose.JWK.asKey(sessionPopKeyPair.privateKey, "pem");
let jwk = (await jose.JWK.asKey(sessionPopKeyPair.publicKey, "pem")).toJSON(true);;
jwk.use = "sig";
jwk.alg = "ES256";
let jwtToken = await jose.JWS.createSign({ "format": 'compact', "fields": { "typ": 'dpop+jwt', "jwk": jwk } }, { "key": privateKey, "reference": false }).update(JSON.stringify(payload)).final();
return jwtToken;
} catch (error) {
logger.error("generateDpop error", error);
throw constant.ERROR_GENERATE_DPOP;
}
};NOTE: Person APIs only
Access Tokens are in JWT format. This JWT complies to the standard 'JSON Web Token (JWT) Profile for OAuth 2.1 Client Authentication and Authorization Grants' (https://tools.ietf.org/html/rfc7523). Partner will need to verify the token with Authorise's public signing key in Authorise's JWKS endpoint.
Sample Code in NodeJS
// Sample Code for Verifying & Decoding JWS or JWT
async function verifyJWS(compactJWS, JWKSUrl) => {
var jwks = await getJwks(JWKSUrl);
try {
let keyStore = await jose.JWK.asKeyStore(jwks);
let result = await jose.JWS.createVerify(keyStore).verify(compactJWS);
let payload = JSON.parse(Buffer.from(result.payload).toString());
return payload;
} catch (error) {
throw "Error with verifying JWS";
}
}
NOTE: Person APIs in Test and Production environments only
The response payload for the Person API (for test and production environments) is first signed, then encrypted:
- Signing is done using JWS (JSON Web Signature) format
- Encryption is done using JWE (JSON Web Encryption) Compact Serialization format
Encryption protects the data at rest while a signed payload means, if necessary, partner will be able to pass this signed payload to a 3rd party where they can verify the payload's integrity with Myinfo's public signing key in Myinfo's JWKS endpoint.
In order to read the payload, partner has to perform the following steps in order:
- Decrypt the payload with the partner's private encryption key corresponding to the partner's encryption public key in the onboarded partner's JWKS endpoint.
- Validate the decrypted payload signature with Myinfo's public signing key return from Myinfo's JWKS endpoint.
After doing the above steps, partner's application will be able to extract the payload in JSON format.
STEP 1: Decryption
- Encryption is done using partner's public encryption key provided in partner's onboarded JWKS endpoint. Decryption of the payload should be using the partner's private encryption key of that key-pair.
- Current encryption algorithms used:
- ECDH-ES+A256KW (for content key wrapping)
- A256GCM (for content encrytion)
Sample Code in NodeJS
// Sample Code for decrypting JWE
async function decryptJWEWithKey(compactJWE, encryptionPrivateKey) {
try {
let keystore = jose.JWK.createKeyStore();
let jweParts = compactJWE.split("."); // header.encryptedKey.iv.ciphertext.tag
if (jweParts.length != 5) {
throw constant.ERROR_INVALID_DATA_OR_SIGNATURE;
}
//Session encryption private key should correspond to the session encryption public key passed in to client assertion
let key = await keystore.add(encryptionPrivateKey, "pem");
let data = {
"type": "compact",
"protected": jweParts[0],
"encrypted_key": jweParts[1],
"iv": jweParts[2],
"ciphertext": jweParts[3],
"tag": jweParts[4],
"header": JSON.parse(jose.util.base64url.decode(jweParts[0]).toString())
};
let result = await jose.JWE.createDecrypt(key).decrypt(data);
return result.payload.toString();
} catch (error) {
throw constant.ERROR_DECRYPT_JWE;
}
};
STEP 2: Verification of Signature
The decrypted payload is signed according to JWS (JSON Web Signature) format, similar to the access token.
- signature algorithm used is
ES256. - Additional attributes 'iat' (epoch time when the signature is generated) and 'txnid' (unique transaction ID for reconciliation purpose) are included in the JWS header.
Sample Code in NodeJS
// Sample Code for Verifying & Decoding JWS or JWT
function verifyJWS = async (compactJWS, JWKSUrl) => {
var jwks = await getJwks(JWKSUrl);
try {
let keyStore = await jose.JWK.asKeyStore(jwks);
let result = await jose.JWS.createVerify(keyStore).verify(compactJWS);
let payload = JSON.parse(Buffer.from(result.payload).toString());
return payload;
} catch (error) {
throw "Error with verifying JWS";
}
}
The RESTful APIs used HTTP specification standard status codes to indicate the success or failure of each request. Except gateway errors, the response content will be in the following JSON format:
{
"code": "integer (int32)",
"message": "string"
}Refer to the individual API definitions for the error codes partner might encounter for each API.
Please refer to the NDI {api} Portal for the following supporting materials where relevant:
- MyInfo demo app
- Code reference tables
- Test accounts for test environments
- Reference user journey templates
For technical queries, contact support@myinfo.gov.sg. For business queries, contact partner@myinfo.gov.sg.
OAuth2
The following are the available OAuth2 scopes for MyInfo APIs
| Security Scheme Type | OAuth2 |
|---|---|
| authorizationCode OAuth Flow | Authorization URL: /com/v4/authorize Token URL: /com/v4/token Scopes:
|
Person-Sample
Retrieves a sample Person data from MyInfo based on UIN/FIN.
This API does not use OAuth2.0 to perform authentication or authorisation, and does not require authorisation token and digital signature.
Note: Null value indicates that an attribute is unavailable.
path Parameters
| uinfin required | string Example: S9812381D |
query Parameters
| scope | Array of strings Example: scope=name hanyupinyinname Space separated list of scope requested. Possible scopes are listed in the scopes of the OAuth2 Security Schema above. |
Responses
Request samples
- Shell
curl https://sandbox.api.myinfo.gov.sg/com/v4/person-sample/S9812381DResponse samples
- 200
{- "partialuinfin": {
- "value": "*****111D",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "uinfin": {
- "value": "S1111111D",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "name": {
- "value": "TAN XIAO HUI",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "hanyupinyinname": {
- "value": "CHEN XIAO HUI",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "aliasname": {
- "value": "TRICIA TAN XIAO HUI",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "hanyupinyinaliasname": {
- "value": "TRICIA CHEN XIAO HUI",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "marriedname": {
- "value": "",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "sex": {
- "code": "F",
- "desc": "FEMALE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "race": {
- "code": "CN",
- "desc": "CHINESE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "secondaryrace": {
- "code": "EU",
- "desc": "EURASIAN",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "dialect": {
- "code": "SG",
- "desc": "SWISS GERMAN",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "nationality": {
- "code": "SG",
- "desc": "SINGAPORE CITIZEN",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "dob": {
- "value": "1958-05-17",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "birthcountry": {
- "code": "SG",
- "desc": "SINGAPORE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "residentialstatus": {
- "code": "C",
- "desc": "CITIZEN",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passportnumber": {
- "value": "E35463874W",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passportexpirydate": {
- "value": "2020-01-01",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "regadd": {
- "type": "SG",
- "block": {
- "value": "548"
}, - "building": {
- "value": ""
}, - "floor": {
- "value": "09"
}, - "unit": {
- "value": "128"
}, - "street": {
- "value": "BEDOK NORTH AVENUE 1"
}, - "postal": {
- "value": "460548"
}, - "country": {
- "code": "SG",
- "desc": "SINGAPORE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "housingtype": {
- "code": "123",
- "desc": "TERRACE HOUSE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "hdbtype": {
- "code": "112",
- "desc": "2-ROOM FLAT (HDB)",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "hdbownership": [
- {
- "noofowners": {
- "value": 2
}, - "address": {
- "type": "SG",
- "block": {
- "value": "548"
}, - "building": {
- "value": ""
}, - "floor": {
- "value": "09"
}, - "unit": {
- "value": "128"
}, - "street": {
- "value": "BEDOK NORTH AVENUE 1"
}, - "postal": {
- "value": "460548"
}, - "country": {
- "code": "SG",
- "desc": "SINGAPORE"
}
}, - "hdbtype": {
- "code": "112",
- "desc": "2-ROOM FLAT (HDB)"
}, - "leasecommencementdate": {
- "value": "2008-06-13"
}, - "termoflease": {
- "value": 99
}, - "dateofpurchase": {
- "value": "2008-06-13"
}, - "dateofownershiptransfer": {
- "value": "2018-06-13"
}, - "loangranted": {
- "value": 310000.01
}, - "originalloanrepayment": {
- "value": 25
}, - "balanceloanrepayment": {
- "years": {
- "value": 2
}, - "months": {
- "value": 6
}
}, - "outstandingloanbalance": {
- "value": 50000.01
}, - "monthlyloaninstalment": {
- "value": 1000.01
}, - "outstandinginstalment": {
- "value": 1000.01
}, - "purchaseprice": {
- "value": 1000.01
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
], - "ownerprivate": {
- "value": false,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "email": {
- "value": "test@gmail.com",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "mobileno": {
- "prefix": {
- "value": "+"
}, - "areacode": {
- "value": "65"
}, - "nbr": {
- "value": "66132665"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "marital": {
- "code": "2",
- "desc": "MARRIED",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "marriagecertno": {
- "value": "123456789012345",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "countryofmarriage": {
- "code": "SG",
- "desc": "SINGAPORE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "marriagedate": {
- "value": "2007-01-01",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "divorcedate": {
- "value": "",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "childrenbirthrecords": [
- {
- "birthcertno": {
- "value": "S5562882C"
}, - "name": {
- "value": "Jo Tan Pei Ni"
}, - "hanyupinyinname": {
- "value": "Cheng Pei Ni"
}, - "aliasname": {
- "value": ""
}, - "hanyupinyinaliasname": {
- "value": ""
}, - "marriedname": {
- "value": ""
}, - "sex": {
- "code": "F",
- "desc": "FEMALE"
}, - "race": {
- "code": "CN",
- "desc": "CHINESE"
}, - "secondaryrace": {
- "code": "",
- "desc": ""
}, - "dialect": {
- "code": "HK",
- "desc": "HOKKIEN"
}, - "lifestatus": {
- "code": "D",
- "desc": "DECEASED"
}, - "dob": {
- "value": "2011-09-10"
}, - "tob": {
- "value": "0901"
}, - "vaccinationrequirements": [
- {
- "requirement": {
- "code": "1M3D",
- "desc": "MINIMUM VACCINATION REQUIREMENT FOR PRESCHOOL"
}, - "fulfilled": {
- "value": true
}
}
], - "sgcitizenatbirthind": {
- "value": "Y"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
], - "sponsoredchildrenrecords": [
- {
- "nric": {
- "value": "S5562882C"
}, - "name": {
- "value": "Jo Tan Pei Ni"
}, - "hanyupinyinname": {
- "value": "Cheng Pei Ni"
}, - "aliasname": {
- "value": ""
}, - "hanyupinyinaliasname": {
- "value": ""
}, - "marriedname": {
- "value": ""
}, - "sex": {
- "code": "F",
- "desc": "FEMALE"
}, - "race": {
- "code": "CN",
- "desc": "CHINESE"
}, - "secondaryrace": {
- "code": "",
- "desc": ""
}, - "dialect": {
- "code": "HK",
- "desc": "HOKKIEN"
}, - "dob": {
- "value": "2011-09-10"
}, - "birthcountry": {
- "code": "SG",
- "desc": "SINGAPORE"
}, - "lifestatus": {
- "code": "A",
- "desc": "ALIVE"
}, - "residentialstatus": {
- "code": "C",
- "desc": "Citizen"
}, - "nationality": {
- "code": "SG",
- "desc": "SINGAPORE CITIZEN"
}, - "scprgrantdate": {
- "value": "2015-06-13"
}, - "vaccinationrequirements": [
- {
- "requirement": {
- "code": "1M3D",
- "desc": "MINIMUM VACCINATION REQUIREMENT FOR PRESCHOOL"
}, - "fulfilled": {
- "value": true
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
], - "occupation": {
- "value": "",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "employment": {
- "value": "ALPHA",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passtype": {
- "code": "RPass",
- "desc": "Work Permit",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passstatus": {
- "value": "Live",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passexpirydate": {
- "value": "2022-12-31",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "employmentsector": {
- "value": "MANUFACTURING",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "vehicles": [
- {
- "vehicleno": {
- "value": "SDF1235A"
}, - "type": {
- "value": "PASSENGER MOTOR CAR"
}, - "iulabelno": {
- "value": ""
}, - "make": {
- "value": "TOYOTA"
}, - "model": {
- "value": "COROLLA ALTIS"
}, - "chassisno": {
- "value": "ZC11S1735800"
}, - "engineno": {
- "value": "M13A1837453"
}, - "motorno": {
- "value": ""
}, - "yearofmanufacture": {
- "value": "2010"
}, - "firstregistrationdate": {
- "value": "2010-06-06"
}, - "originalregistrationdate": {
- "value": "2010-06-06"
}, - "coecategory": {
- "value": "A - CAR UP TO 1600CC & 97KW (130BHP)"
}, - "coeexpirydate": {
- "value": "2020-06-05"
}, - "roadtaxexpirydate": {
- "value": "2020-06-05"
}, - "quotapremium": {
- "value": 14000.01
}, - "openmarketvalue": {
- "value": 25000.01
}, - "co2emission": {
- "value": 146.01
}, - "status": {
- "code": "1",
- "desc": "LIVE"
}, - "primarycolour": {
- "value": "BLACK"
}, - "secondarycolour": {
- "value": "WHITE"
}, - "attachment1": {
- "value": "DISABLED"
}, - "attachment2": {
- "value": "WITH SUN ROOF"
}, - "attachment3": {
- "value": "SIDE CURTAIN"
}, - "scheme": {
- "value": "REVISED OFF-PEAK CAR"
}, - "thcemission": {
- "value": 1.011001
}, - "coemission": {
- "value": 1.100001
}, - "noxemission": {
- "value": 0.011001
}, - "pmemission": {
- "value": 0.007
}, - "enginecapacity": {
- "value": 1600
}, - "powerrate": {
- "value": 1.41
}, - "effectiveownership": {
- "value": "2010-08-31T20:12:12+08:00"
}, - "propellant": {
- "value": "Compressed Natural Gas"
}, - "maximumunladenweight": {
- "value": 1500
}, - "maximumladenweight": {
- "value": 1795
}, - "minimumparfbenefit": {
- "value": 8770.01
}, - "nooftransfers": {
- "value": 2
}, - "vpc": {
- "value": "1234567890"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
], - "drivinglicence": {
- "comstatus": {
- "code": "Y",
- "desc": "ELIGIBLE"
}, - "totaldemeritpoints": {
- "value": 0
}, - "suspension": {
- "startdate": {
- "value": ""
}, - "enddate": {
- "value": ""
}
}, - "disqualification": {
- "startdate": {
- "value": ""
}, - "enddate": {
- "value": ""
}
}, - "revocation": {
- "startdate": {
- "value": ""
}, - "enddate": {
- "value": ""
}
}, - "pdl": {
- "validity": {
- "code": "V",
- "desc": "VALID"
}, - "expirydate": {
- "value": "2020-06-15"
}, - "classes": [
- {
- "class": {
- "value": "2A"
}
}, - {
- "class": {
- "value": "3A"
}
}, - {
- "class": {
- "value": "4P"
}
}, - {
- "class": {
- "value": "4AP"
}
}, - {
- "class": {
- "value": "5P"
}
}
]
}, - "qdl": {
- "validity": {
- "code": "V",
- "desc": "VALID"
}, - "expirydate": {
- "value": "2020-06-15"
}, - "classes": [
- {
- "class": {
- "value": "2A"
}, - "issuedate": {
- "value": "2018-06-06"
}
}, - {
- "class": {
- "value": "3A"
}, - "issuedate": {
- "value": "2018-06-06"
}
}, - {
- "class": {
- "value": "4P"
}, - "issuedate": {
- "value": "2018-06-06"
}
}, - {
- "class": {
- "value": "4AP"
}, - "issuedate": {
- "value": "2018-06-06"
}
}, - {
- "class": {
- "value": "5P"
}, - "issuedate": {
- "value": "2018-06-06"
}
}
]
}, - "photocardserialno": {
- "value": "115616"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "academicqualifications": {
- "transcripts": [
- {
- "name": {
- "value": "SINGAPORE-CAMBRIDGE GENERAL CERTIFICATE OF EDUCATION ORDINARY LEVEL"
}, - "yearattained": {
- "value": "2018"
}, - "results": [
- {
- "subject": {
- "value": "English Language"
}, - "level": {
- "value": "Ordinary"
}, - "grade": {
- "value": "A"
}, - "subsubject": {
- "value": "SPECIAL PAPER"
}, - "subgrade": {
- "value": "One"
}
}
], - "explanatorynotes": {
- "value": "string"
}
}
], - "certificates": [
- {
- "name": {
- "value": "nus.opencert"
}, - "content": {
- "value": "string"
}, - "opencertificate": {
- "id": {
- "value": 100000000343840
}, - "primary": {
- "value": true
}
}, - "opencertificateindicator": {
- "value": true
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "ltavocationallicences": {
- "tdvl": {
- "licencename": {
- "value": "TAXI DRIVER'S VOCATIONAL LICENCE (TDVL)"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "pdvl": {
- "licencename": {
- "value": "PRIVATE HIRE CAR DRIVER'S VOCATIONAL LICENCE (PDVL)"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "bdvl": {
- "licencename": {
- "value": "BUS DRIVER'S VOCATIONAL LICENCE (BDVL)"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "bavl": {
- "licencename": {
- "value": "BUS ATTENDANT VOCATIONAL LICENCE (BAVL)"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "odvl": {
- "licencename": {
- "value": "OMNIBUS DRIVER'S VOCATIONAL LICENCE"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
}, - "chas": {
- "cardtype": {
- "code": "C",
- "desc": "Green"
}, - "indicator": {
- "code": "C",
- "desc": "Green"
}, - "expirydate": {
- "value": "2020-06-15"
}, - "issuedate": {
- "value": "2020-06-15"
}, - "lastupdated": "2019-03-26",
- "name": {
- "value": "TAN XIAO HUI"
}, - "classification": "C",
- "source": "1"
}, - "merdekagen": {
- "eligibility": {
- "value": true
}, - "quantum": {
- "value": 100
}, - "message": {
- "code": "2",
- "desc": "You are eligible for the Merdeka Generation Package. For further enquiries, please contact 1800-2222-888."
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "pioneergen": {
- "eligibility": {
- "value": true
}, - "quantum": {
- "value": 100
}, - "message": {
- "code": "2",
- "desc": "You are eligible for the Pioneer Generation Package. For further enquiries, please contact 1800-2222-888."
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "noa-basic": {
- "amount": {
- "value": 100000.01
}, - "yearofassessment": {
- "value": "2018"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "noa": {
- "amount": {
- "value": 100000.01
}, - "yearofassessment": {
- "value": "2018"
}, - "employment": {
- "value": 100000.01
}, - "trade": {
- "value": 0
}, - "rent": {
- "value": 0
}, - "interest": {
- "value": 0
}, - "taxclearance": {
- "value": "N"
}, - "category": {
- "value": "ORIGINAL"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "noahistory-basic": {
- "noas": [
- {
- "amount": {
- "value": 100000.01
}, - "yearofassessment": {
- "value": "2018"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "noahistory": {
- "noas": [
- {
- "amount": {
- "value": 100000.01
}, - "yearofassessment": {
- "value": "2018"
}, - "employment": {
- "value": 100000.01
}, - "trade": {
- "value": 0
}, - "rent": {
- "value": 0
}, - "interest": {
- "value": 0
}, - "taxclearance": {
- "value": "N"
}, - "category": {
- "value": "ORIGINAL"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfcontributions": {
- "history": [
- {
- "date": {
- "value": "2016-12-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2016-11"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2016-12-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2016-12-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-01-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-01-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-01-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-02-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-02-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-02-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-03-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-03-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-03-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-04-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-04-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-04-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-05-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-05-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-05-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-06-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-06-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-06-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-07-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-07-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-07-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-08-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-08-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-08-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-09-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-09-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-09-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-10-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-10-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-10-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-11-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-11-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-11-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-12-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-12-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-12-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2018-01-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2018-01-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2018-01"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2018-01-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2018-01"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfemployers": {
- "history": [
- {
- "month": {
- "value": "2016-11"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2018-01"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2018-01"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfbalances": {
- "ma": {
- "value": 11470.71,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "oa": {
- "value": 1581.48,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "sa": {
- "value": 21967.09,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "ra": {
- "value": 0.01,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
}, - "cpfhousingwithdrawal": {
- "withdrawaldetails": [
- {
- "address": {
- "type": "SG",
- "block": {
- "value": "548"
}, - "building": {
- "value": ""
}, - "floor": {
- "value": "09"
}, - "unit": {
- "value": "128"
}, - "street": {
- "value": "BEDOK NORTH AVENUE 1"
}, - "postal": {
- "value": "460548"
}, - "country": {
- "code": "SG",
- "desc": "SINGAPORE"
}
}, - "accruedinterestamt": {
- "value": 1581.48
}, - "monthlyinstalmentamt": {
- "value": 1196.09
}, - "principalwithdrawalamt": {
- "value": 2897.01
}, - "totalamountofcpfallowedforproperty": {
- "value": 10000.01
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfhomeprotectionscheme": {
- "coverage": {
- "value": true
}, - "premium": {
- "value": 100.01
}, - "shareofcover": {
- "value": 20
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfdependantprotectionscheme": {
- "coverage": {
- "value": true
}, - "insurercode": {
- "value": "9GEL"
}, - "sumassuredamount": {
- "value": 70000
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfinvestmentscheme": {
- "sdsnetshareholdingqty": {
- "value": 1360,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "account": {
- "agentbankcode": {
- "value": "OCBC"
}, - "invbankacctno": {
- "value": "098-26644-4"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "saqparticipationstatus": {
- "code": "X",
- "desc": "Participated",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
}, - "cpfmedishieldlife": {
- "medishieldlifecoverage": {
- "hascovertag": {
- "value": true
}, - "payername": {
- "value": "string"
}, - "netpremiumpayable": {
- "value": 1000
}, - "policyrenewaldate": {
- "value": "2019-07-02"
}
}, - "integratedshieldplancoverage": {
- "hascovertag": {
- "value": true
}, - "payername": {
- "value": "string"
}, - "insurercode": {
- "value": "string"
}
}, - "medishieldlifedependants": [
- {
- "dependantname": {
- "value": "string"
}, - "netpremiumpayable": {
- "value": 1000
}, - "policyrenewaldate": {
- "value": "2019-07-02"
}
}
], - "integratedshieldplandependants": [
- {
- "dependantname": {
- "value": "string"
}, - "insurercode": {
- "value": "string"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfrstucurrentyeartaxrelief": {
- "totaltaxreliefself": {
- "value": 1000
}, - "remainingtaxreliefself": {
- "value": 1000
}, - "totaltaxrelieflovedones": {
- "value": 1000
}, - "remainingtaxrelieflovedones": {
- "value": 1000
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfrstuselftopupamount": {
- "selftopupusingcash": {
- "value": 1000
}, - "selftopupusingcpf": {
- "value": 1000
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpflife": {
- "cpflifecoverage": {
- "value": true
}, - "cpflifeplan": {
- "value": "Standard Plan"
}, - "cpflifemonthlypayout": {
- "value": 1000
}, - "cpflifepaymentcommencement": {
- "value": true
}, - "cpflifepaymentdate": {
- "value": "2019-09-02"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfmonthlypayouts": {
- "monthlypayout": {
- "value": 1000
}, - "paymentcommencement": {
- "value": true
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
}Token
This API generates an access token when presented with a valid authcode obtained from the Authorise API. This token can then be used to request for the user's data that were consented.
Authorizations:
header Parameters
| DPoP required | string DPoP Proof (JWT) containing the partner's ephemeral public signing key that can be used to prove legit possession of the access token issued. |
Request Body schema: application/x-www-form-urlencoded
| code required | string The authcode given by the authorise API. |
| grant_type required | string Default: "authorization_code" Grant type for getting token (default "authorization_code") |
| client_id required | string Unique ID for your application. |
| redirect_uri required | string Application's callback URL. |
| client_assertion required | string The assertion being used to authenticate the client. Refer to the Security section on Client Assertion for more details. |
| client_assertion_type required | string Default: "urn:ietf:params:oauth:client-assertion-type:jwt-bearer" The format of the assertion, which is defined to be 'urn:ietf:params:oauth:client-assertion-type:jwt-bearer' |
| code_verifier required | string Cryptograhic random string generated and kept secret on serverside. Used to compare with code_challenge sent in the authorize call |
Responses
Request samples
- NodeJS
//get access token using authcode async function getAccessToken(authCode, privateSigningKey, codeVerifier, sessionPopKeyPair) { try { let tokenUrl = process.env.MYINFO_API_TOKEN_URL; let redirectUrl = process.env.PARTNER_REDIRECT_URL; let clientId = process.env.MYINFO_APP_CLIENT_ID; let cacheCtl = "no-cache"; let contentType = "application/x-www-form-urlencoded"; let method = constant.HTTP_METHOD.POST; let clientAssertionType = "urn:ietf:params:oauth:client-assertion-type:jwt-bearer"; let jktThumbprint = await generateJwkThumbprint(sessionPopKeyPair.publicKey) let clientAssertion = await generateClientAssertion(tokenUrl, clientId, privateSigningKey, jktThumbprint); // assemble params for Token API let strParams = `grant_type=authorization_code` + "&code=" + authCode + "&redirect_uri=" + redirectUrl + "&client_id=" + clientId + "&code_verifier=" + codeVerifier + "&client_assertion_type=" + clientAssertionType + "&client_assertion=" + clientAssertion let params = querystring.parse(strParams); let dPoP = await generateDpop(tokenUrl, null,constant.HTTP_METHOD.POST, sessionPopKeyPair); // assemble headers for Token API let strHeaders = `Content-Type=${contentType}&Cache-Control=${cacheCtl}&DPoP=${dPoP}`; let headers = querystring.parse(strHeaders); // invoke Token API let parsedTokenUrl = urlParser.parse(url); let tokenDomain = parsedTokenUrl.hostname; let tokenRequestPath = parsedTokenUrl.path; return getHttpsResponse(hostname, path, headers, method, params); } catch (error) { throw error; };
Response samples
- 200
- 400
- 401
- 403
- 500
{- "access_token": {
- "sub": "string",
- "scope": "string",
- "nbf": "string",
- "iss": "string",
- "txnid": "string",
- "client": {
- "client_id": "STG2-MYINFO-SELF-TEST",
- "client_name": "Myinfo Self Test App",
- "entity_uen": "T16GB0002G",
- "entity_name": "GovTech"
}, - "subentity": {
- "subclient_id": "string",
- "subclient_name": "string",
- "entity_name": "string",
- "entity_uen": "string",
- "whitelist": true
}, - "expires_in": "string",
- "iat": "string",
- "exp": "string",
- "realm": "string",
- "aud": "string",
- "jti": "string",
- "cnf": {
- "jkt": "string"
}, - "jku": "string",
- "epk": {
- "use": "enc",
- "alg": "ECDH-ES+A256KW",
- "kty": "EC",
- "kid": "M-JXqh0gh1GGUUdzNue3IUDyUiagqjHathnscUk2nS8",
- "crv": "P-256",
- "x": "qrR8PAUO6fDouV-6mVdix5IyrVMtu0PVS0nOqWBZosA",
- "y": "6xSbySYW6ke2V727TCgSOPiH4XSDgxFCUrAAMSbl9tI"
}
}, - "token_type": "Bearer",
- "expires_in": 0,
- "scope": "string"
}Person
This API returns user's data from MyInfo when presented with a valid access token obtained from the Token API.
Note: Null value indicates that an attribute is unavailable.
path Parameters
| sub required | string Example: 9E9B2260-47B8-455B-89B5-C48F4DB98322 Identifier of user obtained from 'sub' attribute in access token. May be UINFIN or UUID. |
query Parameters
| scope required | Array of strings Example: scope=name hanyupinyinname Space separated list of scopes requested. Possible scopes are listed in the scopes of the OAuth2 Security Schema above. |
| subentity_id | string Example: subentity_id=180099736H UEN of SaaS partner's client that will be receiving the person data. |
header Parameters
| Authorization required | any Include the access token (JWT) from /token API in this header prefixed with 'DPoP'. |
| DPoP required | any Include the generated Demonstration of Proof of Possession token. |
Responses
Request samples
- NodeJS
// function to prepare request for PERSON API callPersonAPI = async function (uuid, accessToken, sessionEphemeralKeyPair) { let urlLink; urlLink = CONFIG.PERSON_URL + '/' + uuid; let cacheCtl = 'no-cache'; let method = constant.HTTP_METHOD.GET; // assemble params for Person API let strParams = 'scope=' + encodeURIComponent(CONFIG.SCOPE); // assemble headers for Person API let strHeaders = 'Cache-Control=' + cacheCtl; let headers = querystring.parse(strHeaders); //generate ath to append into DPoP let ath = this.securityHelper.base64URLEncode(this.securityHelper.sha256(accessToken)); //generate DPoP let dpopToken = await this.securityHelper.generateDpop(urlLink, ath, method, sessionEphemeralKeyPair); headers['dpop'] = dpopToken; headers['Authorization'] = 'DPoP ' + accessToken; // invoke entity person API let personURL = CONFIG.PERSON_URL; let parsedUrl = urlParser.parse(personURL); let domain = parsedUrl.hostname; let requestPath = parsedUrl.path + '/' + uuid + '?' + strParams; //invoking https to do GET call let personData = await requestHandler.getHttpsResponse(method, 'https://' + domain + requestPath, headers, null, null); return personData.data; };
Response samples
- 200
- 401
- 403
- 404
- 500
{- "partialuinfin": {
- "value": "*****111D",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "uinfin": {
- "value": "S1111111D",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "name": {
- "value": "TAN XIAO HUI",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "hanyupinyinname": {
- "value": "CHEN XIAO HUI",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "aliasname": {
- "value": "TRICIA TAN XIAO HUI",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "hanyupinyinaliasname": {
- "value": "TRICIA CHEN XIAO HUI",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "marriedname": {
- "value": "",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "sex": {
- "code": "F",
- "desc": "FEMALE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "race": {
- "code": "CN",
- "desc": "CHINESE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "secondaryrace": {
- "code": "EU",
- "desc": "EURASIAN",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "dialect": {
- "code": "SG",
- "desc": "SWISS GERMAN",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "nationality": {
- "code": "SG",
- "desc": "SINGAPORE CITIZEN",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "dob": {
- "value": "1958-05-17",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "birthcountry": {
- "code": "SG",
- "desc": "SINGAPORE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "residentialstatus": {
- "code": "C",
- "desc": "CITIZEN",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passportnumber": {
- "value": "E35463874W",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passportexpirydate": {
- "value": "2020-01-01",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "regadd": {
- "type": "SG",
- "block": {
- "value": "548"
}, - "building": {
- "value": ""
}, - "floor": {
- "value": "09"
}, - "unit": {
- "value": "128"
}, - "street": {
- "value": "BEDOK NORTH AVENUE 1"
}, - "postal": {
- "value": "460548"
}, - "country": {
- "code": "SG",
- "desc": "SINGAPORE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "housingtype": {
- "code": "123",
- "desc": "TERRACE HOUSE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "hdbtype": {
- "code": "112",
- "desc": "2-ROOM FLAT (HDB)",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "hdbownership": [
- {
- "noofowners": {
- "value": 2
}, - "address": {
- "type": "SG",
- "block": {
- "value": "548"
}, - "building": {
- "value": ""
}, - "floor": {
- "value": "09"
}, - "unit": {
- "value": "128"
}, - "street": {
- "value": "BEDOK NORTH AVENUE 1"
}, - "postal": {
- "value": "460548"
}, - "country": {
- "code": "SG",
- "desc": "SINGAPORE"
}
}, - "hdbtype": {
- "code": "112",
- "desc": "2-ROOM FLAT (HDB)"
}, - "leasecommencementdate": {
- "value": "2008-06-13"
}, - "termoflease": {
- "value": 99
}, - "dateofpurchase": {
- "value": "2008-06-13"
}, - "dateofownershiptransfer": {
- "value": "2018-06-13"
}, - "loangranted": {
- "value": 310000.01
}, - "originalloanrepayment": {
- "value": 25
}, - "balanceloanrepayment": {
- "years": {
- "value": 2
}, - "months": {
- "value": 6
}
}, - "outstandingloanbalance": {
- "value": 50000.01
}, - "monthlyloaninstalment": {
- "value": 1000.01
}, - "outstandinginstalment": {
- "value": 1000.01
}, - "purchaseprice": {
- "value": 1000.01
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
], - "ownerprivate": {
- "value": false,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "email": {
- "value": "test@gmail.com",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "mobileno": {
- "prefix": {
- "value": "+"
}, - "areacode": {
- "value": "65"
}, - "nbr": {
- "value": "66132665"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "marital": {
- "code": "2",
- "desc": "MARRIED",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "marriagecertno": {
- "value": "123456789012345",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "countryofmarriage": {
- "code": "SG",
- "desc": "SINGAPORE",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "marriagedate": {
- "value": "2007-01-01",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "divorcedate": {
- "value": "",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "childrenbirthrecords": [
- {
- "birthcertno": {
- "value": "S5562882C"
}, - "name": {
- "value": "Jo Tan Pei Ni"
}, - "hanyupinyinname": {
- "value": "Cheng Pei Ni"
}, - "aliasname": {
- "value": ""
}, - "hanyupinyinaliasname": {
- "value": ""
}, - "marriedname": {
- "value": ""
}, - "sex": {
- "code": "F",
- "desc": "FEMALE"
}, - "race": {
- "code": "CN",
- "desc": "CHINESE"
}, - "secondaryrace": {
- "code": "",
- "desc": ""
}, - "dialect": {
- "code": "HK",
- "desc": "HOKKIEN"
}, - "lifestatus": {
- "code": "D",
- "desc": "DECEASED"
}, - "dob": {
- "value": "2011-09-10"
}, - "tob": {
- "value": "0901"
}, - "vaccinationrequirements": [
- {
- "requirement": {
- "code": "1M3D",
- "desc": "MINIMUM VACCINATION REQUIREMENT FOR PRESCHOOL"
}, - "fulfilled": {
- "value": true
}
}
], - "sgcitizenatbirthind": {
- "value": "Y"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
], - "sponsoredchildrenrecords": [
- {
- "nric": {
- "value": "S5562882C"
}, - "name": {
- "value": "Jo Tan Pei Ni"
}, - "hanyupinyinname": {
- "value": "Cheng Pei Ni"
}, - "aliasname": {
- "value": ""
}, - "hanyupinyinaliasname": {
- "value": ""
}, - "marriedname": {
- "value": ""
}, - "sex": {
- "code": "F",
- "desc": "FEMALE"
}, - "race": {
- "code": "CN",
- "desc": "CHINESE"
}, - "secondaryrace": {
- "code": "",
- "desc": ""
}, - "dialect": {
- "code": "HK",
- "desc": "HOKKIEN"
}, - "dob": {
- "value": "2011-09-10"
}, - "birthcountry": {
- "code": "SG",
- "desc": "SINGAPORE"
}, - "lifestatus": {
- "code": "A",
- "desc": "ALIVE"
}, - "residentialstatus": {
- "code": "C",
- "desc": "Citizen"
}, - "nationality": {
- "code": "SG",
- "desc": "SINGAPORE CITIZEN"
}, - "scprgrantdate": {
- "value": "2015-06-13"
}, - "vaccinationrequirements": [
- {
- "requirement": {
- "code": "1M3D",
- "desc": "MINIMUM VACCINATION REQUIREMENT FOR PRESCHOOL"
}, - "fulfilled": {
- "value": true
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
], - "occupation": {
- "value": "",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "employment": {
- "value": "ALPHA",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passtype": {
- "code": "RPass",
- "desc": "Work Permit",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passstatus": {
- "value": "Live",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "passexpirydate": {
- "value": "2022-12-31",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "employmentsector": {
- "value": "MANUFACTURING",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "vehicles": [
- {
- "vehicleno": {
- "value": "SDF1235A"
}, - "type": {
- "value": "PASSENGER MOTOR CAR"
}, - "iulabelno": {
- "value": ""
}, - "make": {
- "value": "TOYOTA"
}, - "model": {
- "value": "COROLLA ALTIS"
}, - "chassisno": {
- "value": "ZC11S1735800"
}, - "engineno": {
- "value": "M13A1837453"
}, - "motorno": {
- "value": ""
}, - "yearofmanufacture": {
- "value": "2010"
}, - "firstregistrationdate": {
- "value": "2010-06-06"
}, - "originalregistrationdate": {
- "value": "2010-06-06"
}, - "coecategory": {
- "value": "A - CAR UP TO 1600CC & 97KW (130BHP)"
}, - "coeexpirydate": {
- "value": "2020-06-05"
}, - "roadtaxexpirydate": {
- "value": "2020-06-05"
}, - "quotapremium": {
- "value": 14000.01
}, - "openmarketvalue": {
- "value": 25000.01
}, - "co2emission": {
- "value": 146.01
}, - "status": {
- "code": "1",
- "desc": "LIVE"
}, - "primarycolour": {
- "value": "BLACK"
}, - "secondarycolour": {
- "value": "WHITE"
}, - "attachment1": {
- "value": "DISABLED"
}, - "attachment2": {
- "value": "WITH SUN ROOF"
}, - "attachment3": {
- "value": "SIDE CURTAIN"
}, - "scheme": {
- "value": "REVISED OFF-PEAK CAR"
}, - "thcemission": {
- "value": 1.011001
}, - "coemission": {
- "value": 1.100001
}, - "noxemission": {
- "value": 0.011001
}, - "pmemission": {
- "value": 0.007
}, - "enginecapacity": {
- "value": 1600
}, - "powerrate": {
- "value": 1.41
}, - "effectiveownership": {
- "value": "2010-08-31T20:12:12+08:00"
}, - "propellant": {
- "value": "Compressed Natural Gas"
}, - "maximumunladenweight": {
- "value": 1500
}, - "maximumladenweight": {
- "value": 1795
}, - "minimumparfbenefit": {
- "value": 8770.01
}, - "nooftransfers": {
- "value": 2
}, - "vpc": {
- "value": "1234567890"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
], - "drivinglicence": {
- "comstatus": {
- "code": "Y",
- "desc": "ELIGIBLE"
}, - "totaldemeritpoints": {
- "value": 0
}, - "suspension": {
- "startdate": {
- "value": ""
}, - "enddate": {
- "value": ""
}
}, - "disqualification": {
- "startdate": {
- "value": ""
}, - "enddate": {
- "value": ""
}
}, - "revocation": {
- "startdate": {
- "value": ""
}, - "enddate": {
- "value": ""
}
}, - "pdl": {
- "validity": {
- "code": "V",
- "desc": "VALID"
}, - "expirydate": {
- "value": "2020-06-15"
}, - "classes": [
- {
- "class": {
- "value": "2A"
}
}, - {
- "class": {
- "value": "3A"
}
}, - {
- "class": {
- "value": "4P"
}
}, - {
- "class": {
- "value": "4AP"
}
}, - {
- "class": {
- "value": "5P"
}
}
]
}, - "qdl": {
- "validity": {
- "code": "V",
- "desc": "VALID"
}, - "expirydate": {
- "value": "2020-06-15"
}, - "classes": [
- {
- "class": {
- "value": "2A"
}, - "issuedate": {
- "value": "2018-06-06"
}
}, - {
- "class": {
- "value": "3A"
}, - "issuedate": {
- "value": "2018-06-06"
}
}, - {
- "class": {
- "value": "4P"
}, - "issuedate": {
- "value": "2018-06-06"
}
}, - {
- "class": {
- "value": "4AP"
}, - "issuedate": {
- "value": "2018-06-06"
}
}, - {
- "class": {
- "value": "5P"
}, - "issuedate": {
- "value": "2018-06-06"
}
}
]
}, - "photocardserialno": {
- "value": "115616"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "academicqualifications": {
- "transcripts": [
- {
- "name": {
- "value": "SINGAPORE-CAMBRIDGE GENERAL CERTIFICATE OF EDUCATION ORDINARY LEVEL"
}, - "yearattained": {
- "value": "2018"
}, - "results": [
- {
- "subject": {
- "value": "English Language"
}, - "level": {
- "value": "Ordinary"
}, - "grade": {
- "value": "A"
}, - "subsubject": {
- "value": "SPECIAL PAPER"
}, - "subgrade": {
- "value": "One"
}
}
], - "explanatorynotes": {
- "value": "string"
}
}
], - "certificates": [
- {
- "name": {
- "value": "nus.opencert"
}, - "content": {
- "value": "string"
}, - "opencertificate": {
- "id": {
- "value": 100000000343840
}, - "primary": {
- "value": true
}
}, - "opencertificateindicator": {
- "value": true
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "ltavocationallicences": {
- "tdvl": {
- "licencename": {
- "value": "TAXI DRIVER'S VOCATIONAL LICENCE (TDVL)"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "pdvl": {
- "licencename": {
- "value": "PRIVATE HIRE CAR DRIVER'S VOCATIONAL LICENCE (PDVL)"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "bdvl": {
- "licencename": {
- "value": "BUS DRIVER'S VOCATIONAL LICENCE (BDVL)"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "bavl": {
- "licencename": {
- "value": "BUS ATTENDANT VOCATIONAL LICENCE (BAVL)"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "odvl": {
- "licencename": {
- "value": "OMNIBUS DRIVER'S VOCATIONAL LICENCE"
}, - "vocationallicencenumber": {
- "value": "E00000001"
}, - "expirydate": {
- "value": "2025-03-30"
}, - "status": {
- "code": "ACT",
- "desc": "ACTIVE"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
}, - "chas": {
- "cardtype": {
- "code": "C",
- "desc": "Green"
}, - "indicator": {
- "code": "C",
- "desc": "Green"
}, - "expirydate": {
- "value": "2020-06-15"
}, - "issuedate": {
- "value": "2020-06-15"
}, - "lastupdated": "2019-03-26",
- "name": {
- "value": "TAN XIAO HUI"
}, - "classification": "C",
- "source": "1"
}, - "merdekagen": {
- "eligibility": {
- "value": true
}, - "quantum": {
- "value": 100
}, - "message": {
- "code": "2",
- "desc": "You are eligible for the Merdeka Generation Package. For further enquiries, please contact 1800-2222-888."
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "pioneergen": {
- "eligibility": {
- "value": true
}, - "quantum": {
- "value": 100
}, - "message": {
- "code": "2",
- "desc": "You are eligible for the Pioneer Generation Package. For further enquiries, please contact 1800-2222-888."
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "noa-basic": {
- "amount": {
- "value": 100000.01
}, - "yearofassessment": {
- "value": "2018"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "noa": {
- "amount": {
- "value": 100000.01
}, - "yearofassessment": {
- "value": "2018"
}, - "employment": {
- "value": 100000.01
}, - "trade": {
- "value": 0
}, - "rent": {
- "value": 0
}, - "interest": {
- "value": 0
}, - "taxclearance": {
- "value": "N"
}, - "category": {
- "value": "ORIGINAL"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "noahistory-basic": {
- "noas": [
- {
- "amount": {
- "value": 100000.01
}, - "yearofassessment": {
- "value": "2018"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "noahistory": {
- "noas": [
- {
- "amount": {
- "value": 100000.01
}, - "yearofassessment": {
- "value": "2018"
}, - "employment": {
- "value": 100000.01
}, - "trade": {
- "value": 0
}, - "rent": {
- "value": 0
}, - "interest": {
- "value": 0
}, - "taxclearance": {
- "value": "N"
}, - "category": {
- "value": "ORIGINAL"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfcontributions": {
- "history": [
- {
- "date": {
- "value": "2016-12-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2016-11"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2016-12-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2016-12-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-01-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-01-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-01-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-02-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-02-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-02-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-03-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-03-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-03-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-04-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-04-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-04-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-05-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-05-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-05-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-06-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-06-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-06-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-07-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-07-12"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-07-21"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-08-01"
}, - "amount": {
- "value": 500
}, - "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "date": {
- "value": "2017-08-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-08-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-09-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-09-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-09-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-10-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-10-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-10-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-11-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-11-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-11-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-12-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-12-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2017-12-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2018-01-01"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2018-01-12"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2018-01"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "date": {
- "value": "2018-01-21"
}, - "amount": {
- "value": 750
}, - "month": {
- "value": "2018-01"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfemployers": {
- "history": [
- {
- "month": {
- "value": "2016-11"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2016-12"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-01"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-02"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-03"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-04"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-05"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-06"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-07"
}, - "employer": {
- "value": "Crystal Horse Invest Pte Ltd"
}
}, - {
- "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-08"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-09"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-10"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-11"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2017-12"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2018-01"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}, - {
- "month": {
- "value": "2018-01"
}, - "employer": {
- "value": "Delta Marine Consultants PL"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfbalances": {
- "ma": {
- "value": 11470.71,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "oa": {
- "value": 1581.48,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "sa": {
- "value": 21967.09,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "ra": {
- "value": 0.01,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
}, - "cpfhousingwithdrawal": {
- "withdrawaldetails": [
- {
- "address": {
- "type": "SG",
- "block": {
- "value": "548"
}, - "building": {
- "value": ""
}, - "floor": {
- "value": "09"
}, - "unit": {
- "value": "128"
}, - "street": {
- "value": "BEDOK NORTH AVENUE 1"
}, - "postal": {
- "value": "460548"
}, - "country": {
- "code": "SG",
- "desc": "SINGAPORE"
}
}, - "accruedinterestamt": {
- "value": 1581.48
}, - "monthlyinstalmentamt": {
- "value": 1196.09
}, - "principalwithdrawalamt": {
- "value": 2897.01
}, - "totalamountofcpfallowedforproperty": {
- "value": 10000.01
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfhomeprotectionscheme": {
- "coverage": {
- "value": true
}, - "premium": {
- "value": 100.01
}, - "shareofcover": {
- "value": 20
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfdependantprotectionscheme": {
- "coverage": {
- "value": true
}, - "insurercode": {
- "value": "9GEL"
}, - "sumassuredamount": {
- "value": 70000
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfinvestmentscheme": {
- "sdsnetshareholdingqty": {
- "value": 1360,
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "account": {
- "agentbankcode": {
- "value": "OCBC"
}, - "invbankacctno": {
- "value": "098-26644-4"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "saqparticipationstatus": {
- "code": "X",
- "desc": "Participated",
- "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
}, - "cpfmedishieldlife": {
- "medishieldlifecoverage": {
- "hascovertag": {
- "value": true
}, - "payername": {
- "value": "string"
}, - "netpremiumpayable": {
- "value": 1000
}, - "policyrenewaldate": {
- "value": "2019-07-02"
}
}, - "integratedshieldplancoverage": {
- "hascovertag": {
- "value": true
}, - "payername": {
- "value": "string"
}, - "insurercode": {
- "value": "string"
}
}, - "medishieldlifedependants": [
- {
- "dependantname": {
- "value": "string"
}, - "netpremiumpayable": {
- "value": 1000
}, - "policyrenewaldate": {
- "value": "2019-07-02"
}
}
], - "integratedshieldplandependants": [
- {
- "dependantname": {
- "value": "string"
}, - "insurercode": {
- "value": "string"
}
}
], - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfrstucurrentyeartaxrelief": {
- "totaltaxreliefself": {
- "value": 1000
}, - "remainingtaxreliefself": {
- "value": 1000
}, - "totaltaxrelieflovedones": {
- "value": 1000
}, - "remainingtaxrelieflovedones": {
- "value": 1000
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfrstuselftopupamount": {
- "selftopupusingcash": {
- "value": 1000
}, - "selftopupusingcpf": {
- "value": 1000
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpflife": {
- "cpflifecoverage": {
- "value": true
}, - "cpflifeplan": {
- "value": "Standard Plan"
}, - "cpflifemonthlypayout": {
- "value": 1000
}, - "cpflifepaymentcommencement": {
- "value": true
}, - "cpflifepaymentdate": {
- "value": "2019-09-02"
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}, - "cpfmonthlypayouts": {
- "monthlypayout": {
- "value": 1000
}, - "paymentcommencement": {
- "value": true
}, - "classification": "C",
- "source": "1",
- "lastupdated": "2019-03-26"
}
}